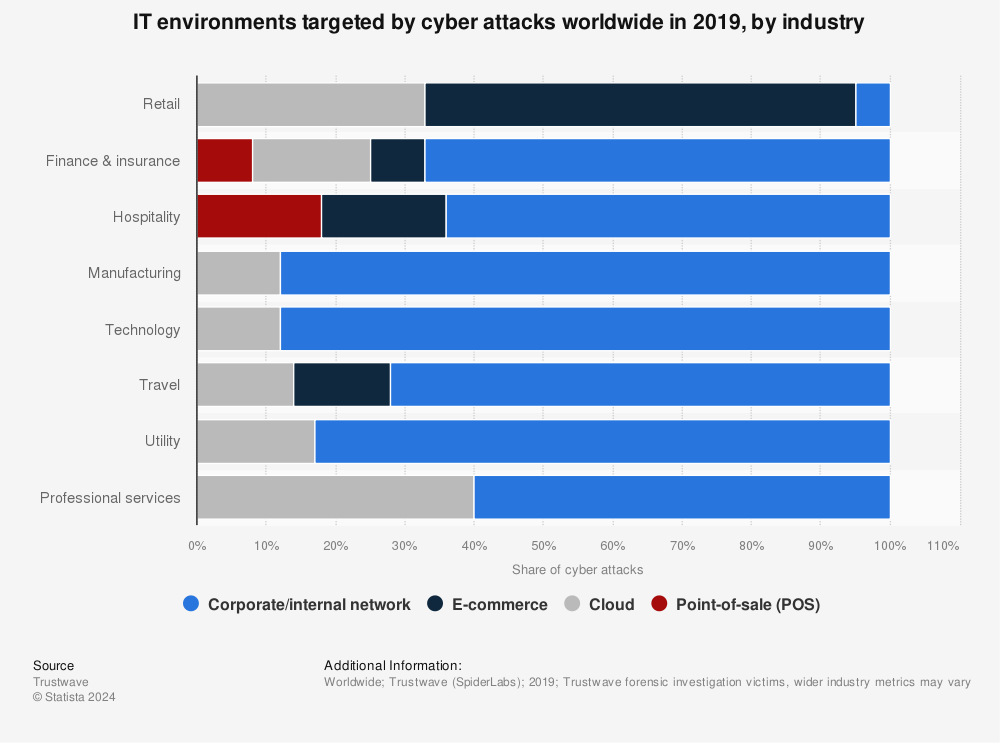
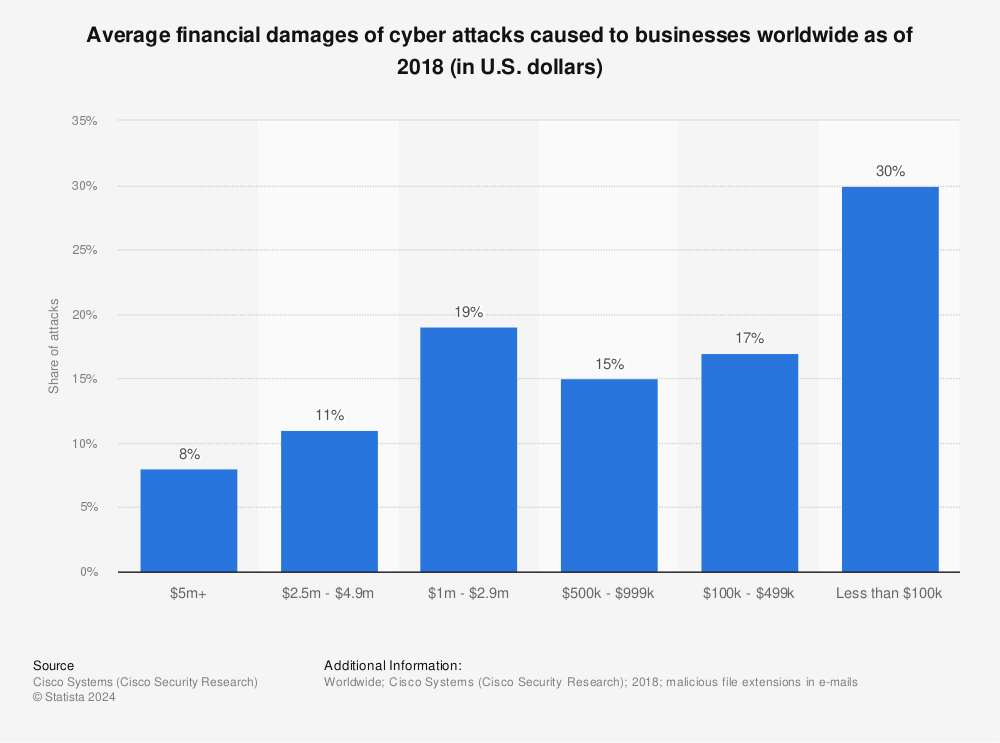
Penetration Testing
Penetration Testing is a controlled real world cyber attack on your infrastructure to gain entry and identify security vulnerabilities BEFORE they are found by others with malicious intent.
Organisations may take many steps to protect their critical cyber assets, but all too often do not systematically and diversely test their cyber defences from a real world threat perspective. As rouge hacking activities advance, we are staying ahead and protect against the most advanced and unforeseen attack elevations by performing them first.
Our certified experts are able to test a broad range of attack vectors including:
- Network Infrastructure
- Web Applications
- Wireless Connectivity
- Mobile Applications
- Employee Cyber Security Awareness